‘Eurograbber’: the £30M Mobile Banking Heist
Published by Gbaf News
Posted on February 15, 2013
6 min readLast updated: January 22, 2026
Published by Gbaf News
Posted on February 15, 2013
6 min readLast updated: January 22, 2026

How a sophisticated fraud using both PC and mobile malware became one of the largest and most successful ever: and the security implications for banks and customers. By Terry Greer-King, UK MD for Check Point, which together with Versafe discovered the fraud
In the history of bank robberies, the £30M ($47M US) stolen by the Eurograbber attack in 2012 ranks as one of the all-time biggest, globally. And when you consider that this sum was stolen from the accounts of over 30,000 customers of over 30 banks in four European countries, using malware that affected both PCs and bank customers’ mobile phones, it must also rank as one of the most sophisticated thefts ever discovered.
But the most worrying aspect of Eurograbber was that it worked within banks’ existing 2-factor authentication security, so that – from the banks’ viewpoint – the fraudulent transactions appeared perfectly legitimate. This helped Eurograbber to remain active and undetected for months, and enabled the criminals behind it to steal more and more cash. So how was the Eurograbber attack able to do this? And how can banks and bank customers protect themselves to avoid such attacks in the future?
The key to Eurograbber’s success was that the hackers behind the attack had an in-depth understanding of how both consumer and business online banking systems work. The attack specifically targeted the two-factor authentication method using one-time passcodes sent by SMS to mobile devices, and relied on intercepting those text messages so that legitimate passcodes could be exploited.
Attacking on two fronts
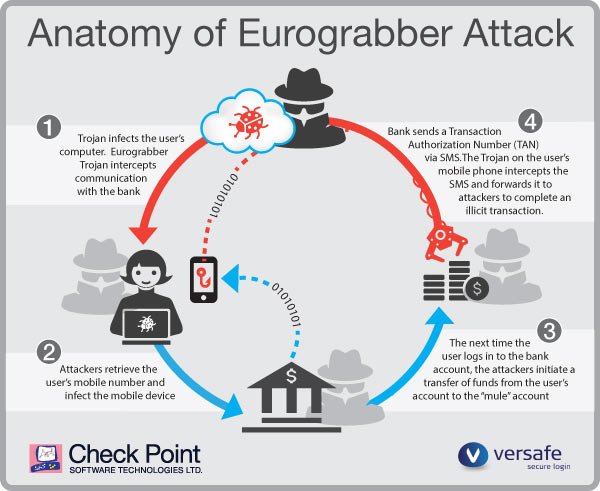
What the attackers did was to develop a 2-stage attack. The first stage involved infecting the bank customer’s PC, and phishing their details. This was done by transparently infecting the customer, using either a phishing e-mail with a malicious link, or by surfing to a malicious link on the web. This downloaded a customised version of the well-known Zeus trojan onto their PC, which lays dormant.
Then, when the bank customer accessed their bank account, the Trojan woke up and launched a fake version of the bank’s web page, containing instructions for ‘upgrading’ the user’s online banking system. As well as asking the user to re-key account numbers and other bank details, it requested their mobile phone details. The page then instructed the user that in order to complete the upgrade, instructions would be sent to their mobile by text, for the user to follow.
This was the second stage of the attack. When the user received the text, which appeared to be from their bank, they were directed to complete the ‘banking upgrade’ by clicking on a web link. However, doing this caused the Zeus in the mobile (ZITMO) Trojan to be downloaded onto their mobile device. If the user had the right type of device – either a Blackberry, Android or Symbian phone – the device was infected.
No need to fake TAN
This completed the circle of infection for the user’s PC and mobile device. Every time they access their bank account online thereafter, the attack initiated a transaction to transfer money out of their account. This worked by the Trojan on the PC recognising that the user was accessing their account, and transparently sending a request to the bank to transfer an amount of money from this account to the attacker’s ‘mule’ account.
When the bank received that request, the bank generated the transaction authentication number (TAN) and sent it via SMS to the bank customer’s mobile device. This was intercepted by the Trojan on the mobile device. The Trojan then used that SMS, extracted the TAN and sent it back to the bank to complete the illicit banking transaction.
The fraudulent transactions were completely transparent to customers, as they didn’t see the bank’s SMS messages on their mobile phone. And to the bank, they looked like legitimate transactions. The attackers even configured the Zeus trojans to restrict the amount transferred in each transaction to a percentage of the account’s balance, helping them to remain undetected.
Security matters
So what security lessons can be drawn from the Eurograbber attack? It was certainly successful in exploiting out-of-band authentication methods, in which a one-time passcode is created and sent to a mobile device, which are quite commonly used in Europe.
While banks that use other authentication methods were not vulnerable to this specific attack, it highlights the fact that exploits can be developed to target specific authentication systems – and that attackers have the patience and resources to do so. Just a couple of years ago, code for the market-leading 2-factor authentication solution was stolen, leading to the risk of hacking – which shows that no authentication solution is invulnerable.
However, it also highlights the critical role that online banking users themselves play in security. Eurograbber targeted customers, not the banks themselves. So the best protection against possible future attacks like Eurograbber is to ensure online banking customers have up-to-date protection in two areas – on the network that gives internet access to their bank, and on the PC they use for online banking.
User protection
It’s worth reiterating to online banking users that their banks should never send an unsolicited email, and so the user should not respond to these, as they will be phishing mails. Users should be encouraged to use up-to-date antivirus software and a firewall on their home PCs. Cost is not an issue here: there are free solutions from ZoneAlarm and others that deliver protection matching leading paid-for products. These solutions will detect variants of the Zeus Trojan before the user’s PC becomes infected.Another key preventative measure is for users to regularly install software updates on PCs, to keep security as current as possible.
If a users’ PCis already infected, the Eurograbber Trojan will try to connect to its Command & Control (C&C) server to complete the infection and to carry out financial transfers out of the bank customer’s account: installing a firewall will block this communication, and an anti-virus update and scan should detect the infection and remove it.
In conclusion, there is no ‘silver bullet’ solution that protects against cyberattacks such as Eurograbber. It’s a matter of ongoing vigilance, and ensuring that the security protections used by banks and their customers are as comprehensive, and as up-to-date as possible.With these measures, there’s the best possible chance that a future attempt at cybercrime won’t pay.
Explore more articles in the Top Stories category











