SSH KEYS: THE HIDDEN COMPLIANCE THREAT
Published by Gbaf News
Posted on July 21, 2017
8 min readLast updated: January 21, 2026

Published by Gbaf News
Posted on July 21, 2017
8 min readLast updated: January 21, 2026

By Fouad Khalil, VP of Compliance, SSH Communications Security

Fouad Khalil
Because the financial industry is one of the most heavily regulated, possible compliance issues lurk around almost every corner. SSH user key-based access is not typically included as one of those issues. But it should be. In many financial institutions, accountability for these keys is unclear, opening the door to compliance violations.
At the heart of the issue is access control. It’s all about protecting the data (PII, credit card data, etc.)and making sure it has authorized access. It doesn’t matter whether access is being requested by a machine, admin or business user. The fact is that:
For example, in some 10,000 Unix/Linux hosts, lack of strong SSH key management equates to 1.5 million application keys granting access and 70,000 keys each for database administrators and system admins. There can be up to one billion authentications per year granting access. The majority of the access available via these keys is obsolete, having been assigned to employees or third parties who no longer work with or for the financial institution.
A Ticking Compliance Bomb
In other words, it’s only a matter of time before this compliance bomb explodes. SSH keys are a critical component of logical, privileged and third-party access; their misuse can have repercussions across all critical frameworks.Regulatory bodies won’t be easing up any time soon – instead, they are issuing seven-figure fines, jail time and reputation-damaging publicity.
For instance, potential fines and jail time await SOX violators, and PCI violations pack their own punch. In addition to stiff fines, PCI can take away your payment processing privileges. This happened to a national chain, rendering the chain incapable of processing card transactions for several weeks. That’s a financially devastating outcome, one that has the potential to destroy a business.
Getting to the Heart ofAccess
Let’s examine the access issue by supposing that you are an auditor in the financial industry. You conduct annual IT General Controls audits for all your in-scope IT systems.You continuously assess the effectiveness of your logical access, privileged access and segregation of duties controls. Now, have you considered SSH keys? Once you learn what those keys are and what they entail, consider that the assumption that someone’s managing them is often wrong.This is the “dark side of compliance.”CEOs and CFOs of publically traded financial institutions are required by law to attest the state of their internal controls annually. Access control is a key component of these attestations, so how accurate are they if SSH key-based access (elevated in nature) is not part of the assessment?
When put into these terms, those responsible for compliance realize that they must take action on SSH-related, key-based access. Then the logical three questions follow:
A vague answer, or no answer at all, to any one or more of these questions means you need to take action immediately.
Proactive Control
Clearly, it can be difficult to take control of SSH user key-based access, but it is possible – and critical. The more security controls you implement as a standard business practice, the more likely you are to be compliant out of the box. Adopt the mindset of continuous compliance. It’s not a matter of checking a box that you set up a server; you need to harden everything that goes on that server. It may seem impossible to do this company-wide, but start with critical assets and then implement in phases.
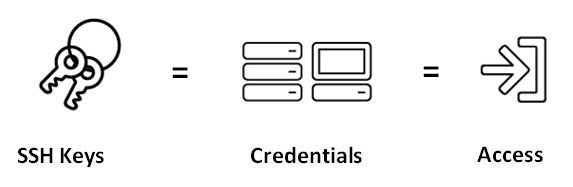
This work must be started immediately to ensure compliance and satisfy the auditors. It must not be done manually, though, in light of the fact that hundreds of thousands of key pairs may be lurking in your infrastructure. Get the assistance of experts who can help walk you through the process in a systematic way, and implement automation. Start today, before a breach or audit occurs. And don’t forget this crucial equation:
By Fouad Khalil, VP of Compliance, SSH Communications Security

Fouad Khalil
Because the financial industry is one of the most heavily regulated, possible compliance issues lurk around almost every corner. SSH user key-based access is not typically included as one of those issues. But it should be. In many financial institutions, accountability for these keys is unclear, opening the door to compliance violations.
At the heart of the issue is access control. It’s all about protecting the data (PII, credit card data, etc.)and making sure it has authorized access. It doesn’t matter whether access is being requested by a machine, admin or business user. The fact is that:
For example, in some 10,000 Unix/Linux hosts, lack of strong SSH key management equates to 1.5 million application keys granting access and 70,000 keys each for database administrators and system admins. There can be up to one billion authentications per year granting access. The majority of the access available via these keys is obsolete, having been assigned to employees or third parties who no longer work with or for the financial institution.
A Ticking Compliance Bomb
In other words, it’s only a matter of time before this compliance bomb explodes. SSH keys are a critical component of logical, privileged and third-party access; their misuse can have repercussions across all critical frameworks.Regulatory bodies won’t be easing up any time soon – instead, they are issuing seven-figure fines, jail time and reputation-damaging publicity.
For instance, potential fines and jail time await SOX violators, and PCI violations pack their own punch. In addition to stiff fines, PCI can take away your payment processing privileges. This happened to a national chain, rendering the chain incapable of processing card transactions for several weeks. That’s a financially devastating outcome, one that has the potential to destroy a business.
Getting to the Heart ofAccess
Let’s examine the access issue by supposing that you are an auditor in the financial industry. You conduct annual IT General Controls audits for all your in-scope IT systems.You continuously assess the effectiveness of your logical access, privileged access and segregation of duties controls. Now, have you considered SSH keys? Once you learn what those keys are and what they entail, consider that the assumption that someone’s managing them is often wrong.This is the “dark side of compliance.”CEOs and CFOs of publically traded financial institutions are required by law to attest the state of their internal controls annually. Access control is a key component of these attestations, so how accurate are they if SSH key-based access (elevated in nature) is not part of the assessment?
When put into these terms, those responsible for compliance realize that they must take action on SSH-related, key-based access. Then the logical three questions follow:
A vague answer, or no answer at all, to any one or more of these questions means you need to take action immediately.
Proactive Control
Clearly, it can be difficult to take control of SSH user key-based access, but it is possible – and critical. The more security controls you implement as a standard business practice, the more likely you are to be compliant out of the box. Adopt the mindset of continuous compliance. It’s not a matter of checking a box that you set up a server; you need to harden everything that goes on that server. It may seem impossible to do this company-wide, but start with critical assets and then implement in phases.
This work must be started immediately to ensure compliance and satisfy the auditors. It must not be done manually, though, in light of the fact that hundreds of thousands of key pairs may be lurking in your infrastructure. Get the assistance of experts who can help walk you through the process in a systematic way, and implement automation. Start today, before a breach or audit occurs. And don’t forget this crucial equation:

Explore more articles in the Top Stories category











