Teradata Revenue Increases 18 Percent in Constant Currency
Published by Gbaf News
Posted on August 6, 2012
11 min readLast updated: January 22, 2026
Published by Gbaf News
Posted on August 6, 2012
11 min readLast updated: January 22, 2026

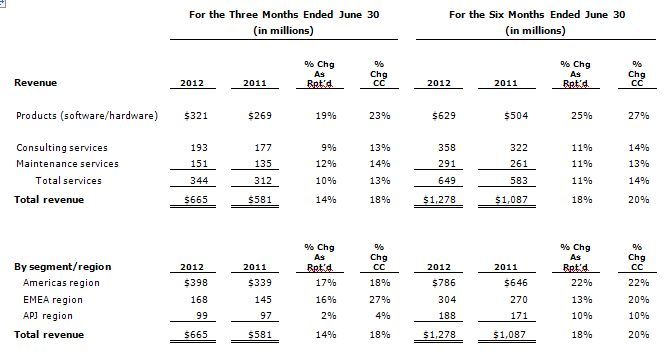
ATLANTA – Teradata Corporation (NYSE: TDC) today reported revenue of $665 million for the quarter ended June 30, 2012, an increase of 14 percent from $581 million in the second quarter of 2011. Currency translation reduced the second quarter revenue comparison by 4 percentage points.(1)
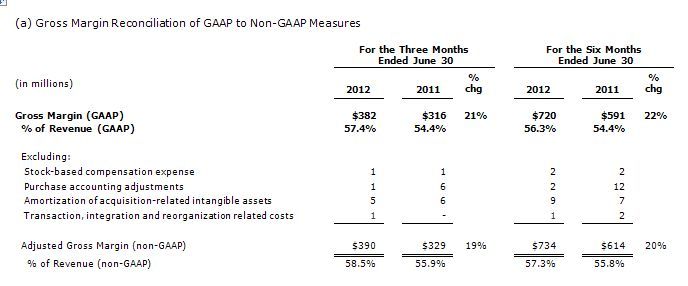
Gross margin of 57.4 percent was up from the 54.4 percent reported in the second quarter of 2011. On a non-GAAP basis, excluding the special items and stock-based compensation expense described in footnote #2,(2) gross margin was 58.5 percent, a 260 basis point improvement from 55.9 percent in the second quarter of 2011. The increase in gross margin was driven by leverage from revenue growth as well as a favorable product and services revenue mix.
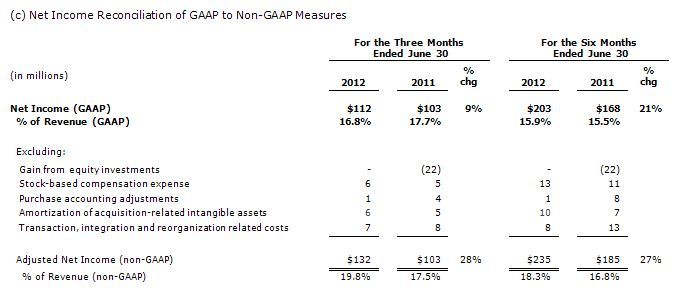
Stock-based compensation expense and special items had a $20 million negative impact on Teradata’s second quarter 2012 net income as reported under U.S. Generally Accepted Accounting Principles (GAAP).(2)
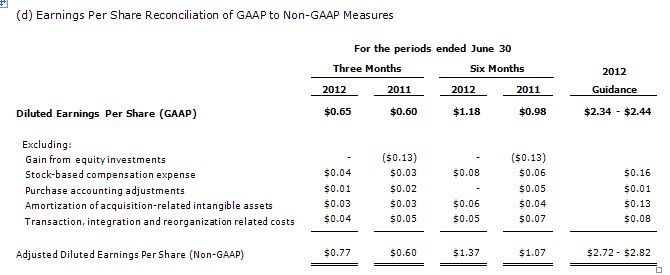
Teradata reported GAAP net income of $112 million, or $0.65 per diluted share, which compared to GAAP net income of $103 million, or $0.60 per diluted share, in the second quarter of 2011. Excluding stock-based compensation expense and the special items detailed in footnote #2,(2) non-GAAP net income in the second quarter of 2012 was $132 million, or $0.77 per diluted share, versus $103 million, or $0.60 per diluted share in the second quarter of 2011.(2)
“Teradata delivered another strong quarter in Q2 with revenue growth of 18 percent in constant currency, and Non-GAAP EPS growth of 28 percent. As a result, we are increasing our guidance for constant currency revenue growth and EPS for 2012,” said Mike Koehler, president and chief executive officer of Teradata Corporation.
“Strong execution across the company led to 20 percent constant currency revenue growth in the first half of 2012 and record operating margin. Our technology leadership and expertise in data warehousing, big data analytics and integrated marketing management uniquely position Teradata to help customers realize the greatest value from their information assets, while enabling them to reduce infrastructure costs.”
Regional Operating Segment Results
Teradata reports its results in three regional operating segments.
Americas
Teradata generated $398 million of revenue in its Americas region, up 17 percent from $339 million in the second quarter of 2011. Currency translation reduced the year-over-year revenue comparison for the Americas region by 1 percentage point.(1)
Europe, Middle East and Africa (EMEA)
Revenue in Teradata’s EMEA region was $168 million, up 16 percent from $145 million generated in the second quarter of 2011. Currency translation reduced the year-over-year revenue comparison for the EMEA region by 11 percentage points.(1)
Asia Pacific / Japan (APJ)
Teradata generated $99 million of revenue in its APJ region, a 2 percent increase from $97 million in the second quarter of 2011. Currency translation reduced the year-over-year comparison in the APJ region by 2 percentage points.(1)
Operating Income
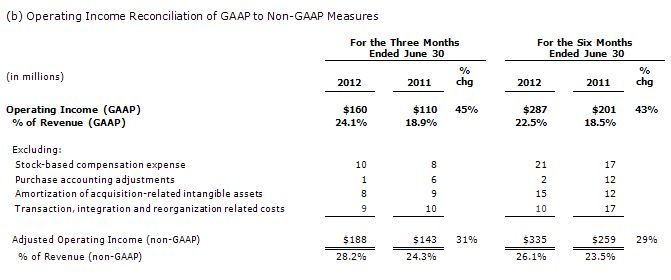
Second-quarter operating income of $160 million increased from $110 million reported in the second quarter of 2011. On a non-GAAP basis, operating income of $188 million increased 31 percent from the second quarter of 2011.(2) Higher revenue as well as favorable product and services revenue mix more than offset the increased investment in selling expense and research and development.
Cash Flow
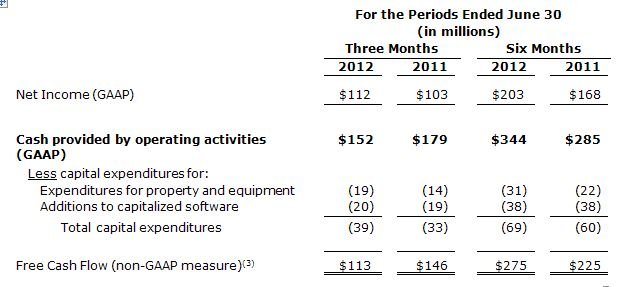
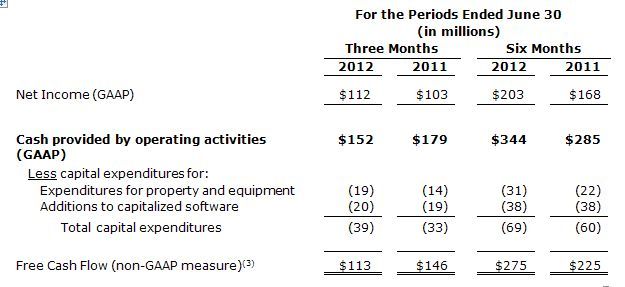
Teradata generated $152 million of cash from operating activities, compared to $179 million in the prior-year period. Teradata generated $113 million of free cash flow (cash from operating activities less capital expenditures and additions to capitalized software)(3) in the second quarter of 2012, versus $146 million in the same period in 2011. The decline in cash from operating activities and free cash flow was due to the timing of balance sheet related items between the first and second quarters of the respective years. See the year-to-date information below which normalizes these timing variances.
Year-to-date, Teradata generated $344 million of cash from operating activities, a $59 million increase from $285 million generated in the first half of 2011. Teradata generated $275 million of free cash flow(3) in the first half of 2012, a $50 million increase from $225 million generated during the same period in 2011.
Balance Sheet
Teradata ended the second quarter of 2012 with $821 million in cash, a $157 million decrease from March 31, 2012. The net decrease was due in part to acquisition and other investing activities during the quarter. Additionally, Teradata repurchased approximately 545,000 shares for $37 million during the quarter.
As of June 30, 2012, Teradata had total debt of $296 million outstanding under a term loan. Additionally, Teradata has $300 million available through a pre-arranged credit facility; however no funds were drawn from the credit facility.
2012 Outlook
Teradata is raising its expectations for constant currency revenue growth from the 13-15 percent revenue range to the 14-16 percent range. However due to currency changes since early May 2012, when Teradata previously provided revenue guidance, Teradata now anticipates that currency translation will negatively impact the year-over-year revenue comparison by an additional percentage point, based on currency rates on July 30, 2012. As a result Teradata’s expectation for 2012 full-year reported revenue growth remains at 12-14 percent.
Teradata is increasing its guidance for 2012 GAAP earnings per share to the range of $2.34 to $2.44. Excluding stock-based compensation expense and special items, non-GAAP EPS for 2012 is now expected to increase to the range of $2.72 to $2.82, versus prior non-GAAP EPS guidance of $2.60 to $2.70.(2)
2012 Second-Quarter Earnings Conference Call
A conference call is scheduled today at 8:30 a.m. (ET) to discuss the company’s second-quarter 2012 results. Access to the conference call, as well as a replay of the call, is available on Teradata’s web site at www.teradata.com/investor.
Supplemental financial information regarding Teradata’s operating results is also available on the Investor Relations page of Teradata’s web site.
About Teradata
Teradata Corporation (NYSE: TDC) is the world’s leading analytic data solutions company, focused on integrated data warehousing, big data analytics, and business applications. Teradata’s innovative products and services deliver data integration and business insight to empower organizations to make the best decisions possible for competitive advantage. Visit teradata.com for details.
1. The impact of currency is determined by calculating the prior-period results using the current-year monthly average currency rates. See the foreign currency schedule on the Investor Relations page of the company’s web site www.teradata.com/investor.
2. Teradata reports its results in accordance with Generally Accepted Accounting Principles in the United States, or GAAP. However, as described below, the company believes that certain non-GAAP measures (such as non-GAAP gross margin, non-GAAP operating income, non-GAAP net income, and non-GAAP earnings per diluted share, or EPS, which exclude certain items as well as free cash flow) are useful for investors. Our non-GAAP measures are not meant to be considered in isolation or as substitutes for, or superior to results determined in accordance with GAAP, and should be read only in conjunction with our condensed consolidated financial statements prepared in accordance with GAAP.
Special items included in Teradata’s second quarter GAAP operating income results as reported in this release included $8 million of amortization of acquisition-related intangible assets; $1 million of acquisition-related purchase accounting adjustments; $9 million of acquisition transaction and integration expenses; and $10 million of stock-based compensation expense.
The following tables reconcile Teradata’s actual and projected results and EPS, under GAAP to the company’s actual and projected non-GAAP results and EPS for the periods presented, which exclude certain items. Our management regularly uses supplemental non-GAAP financial measures, such as gross margin, operating income, net income and EPS, excluding certain items internally, to understand, manage and evaluate our business and support operating decisions. The company believes such non-GAAP financial measures (1) provide useful information to investors regarding the underlying business trends and performance of the company’s ongoing operations, (2) are useful for period-over-period comparisons of such operations and results, that may be more easily compared to peer companies and allow investors a view of the company’s operating results excluding special items, (3) provide useful information to management and investors regarding present and future business trends, and (4) provide consistency and comparability with past reports and projections of future results.
3. As described above, the company believes that free cash flow is a useful non-GAAP measure for investors. Teradata defines free cash flow as cash provided/used by operating activities less capital expenditures for property and equipment, and additions to capitalized software. Free cash flow does not have a uniform definition under GAAP and therefore, Teradata’s definition may differ from other companies’ definitions of this measure. Teradata’s management uses free cash flow to assess the financial performance of the company and believes it is useful for investors because it relates the operating cash flow of the company to the capital that is spent to continue and improve business operations.
In particular, free cash flow indicates the amount of cash generated after capital expenditures for, among other things, investment in the company’s existing businesses, strategic acquisitions, strengthening the company’s balance sheet, repurchase of the company’s stock and repayment of the company’s debt obligations, if any. Free cash flow does not represent the residual cash flow available for discretionary expenditures since there may be other nondiscretionary expenditures that are not deducted from the measure. This non-GAAP measure is not meant to be considered in isolation or as a substitute for, or superior to results determined in accordance with GAAP, and should be read only in conjunction with our condensed consolidated financial statements prepared in accordance with GAAP.
Note to Investors
This news release contains forward-looking statements, including statements as to anticipated or expected results, beliefs, opinions and future financial performance, within the meaning of Section 21E of the Securities and Exchange Act of 1934. Forward-looking statements include projections of revenue, profit growth and other financial items, future economic performance and statements concerning analysts’ earnings estimates, among other things. These forward-looking statements are based on current expectations and assumptions and involve risks and uncertainties that could cause Teradata’s actual results to differ materially. In addition to the factors discussed in this release, other risks and uncertainties could affect our future results, and could cause actual results to differ materially from those expressed in such forward-looking statements. Such factors include those relating to: the global economic environment in general or on the ability of our suppliers to meet their commitments to us, or the timing of purchases by our current and potential customers, and other general economic and business conditions; the rapidly changing and intensely competitive nature of the information technology industry and the data warehousing business, including the increased pressure on price/performance for data warehousing solutions; fluctuations in our operating results, unanticipated delays or accelerations in our sales cycles and the difficulty of accurately estimating revenues; risks inherent in operating in foreign countries, including the impact of economic, political, legal, regulatory, compliance, cultural, foreign currency fluctuations and other conditions abroad; the timely and successful development, production or acquisition and market acceptance of new and existing products and services, including our ability to accelerate market acceptance of new products and services as well as the reliability, quality and operability of new products because of the difficulty and complexity associated with their testing and production; tax rates; turnover of workforce and the ability to attract and retain skilled employees; availability and successful exploitation of new acquisition and alliance opportunities; our ability to execute integration plans for newly acquired entities, including the possibility that expected synergies and operating efficiencies may not be achieved, that such integration efforts may be more difficult, time-consuming or costly than expected, and that operating costs, customer loss and business disruption (including, without limitation, difficulties in maintaining relationships with employees, customers, clients or suppliers) may be greater than expected following the transaction; recurring revenue may decline or fail to be renewed; changes in Generally Accepted Accounting Principles (GAAP) and the resulting impact, if any, on the company’s accounting policies; continued efforts to establish and maintain best-in-class internal information technology and control systems; and other factors described from time-to-time in the company’s filings with the U.S. Securities and Exchange Commission, including its annual report on Form 10-K and subsequent quarterly reports on Forms 10-Q, as well as the company’s annual reports to stockholders. The company does not undertake any obligation to publicly update or revise any forward-looking statements, whether as a result of new information, future events or otherwise.
For media information:
Mike O’Sullivan
(937) 242-4786
mike.osullivan@teradata.com
For investor information:
Gregg Swearingen
(937) 242-4600
gregg.swearingen@teradata.com
Explore more articles in the Top Stories category











